Switching and Layer 2 Security
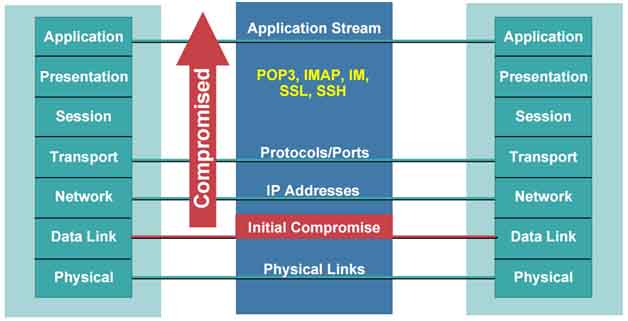
Layer 2 switched environments, typically found in enterprise structured wiring closets, can be easy targets for network security attacks. Failing to secure our switch architecture is like sending hackers an engraved invitation to attack our network.
Network Administration Team, wing of ICTS keep up the security measures in switching environment in the following concerns.
- Using SSH instead of Telnet in the core switches for administration tasks
- Authorized accounts to access switches must be assigned the least privilege level necessary to perform assigned duties
- The devices must not have any default manufacturer password
- Native VLAN is assigned to a VLAN ID other than the default VLAN for all 802.1q trunk links
- Switch access port is not assigned to native VLAN
- Disabled ports are placed in an unused VLAN
- Separate management VLAN is used to manage all switches in the network
- The devices configured to drop half open TCP sessions through filtering threshold and time out period
- Using secure SNMP passwords for ‘read’ and ‘read - write’ operations
- Upgrading the switch software to the latest stable versions
- Using Lock-Learning mechanism to restrict allowed computers only in the switch ports
- Maintaining the physical security to the switches and switch racks
